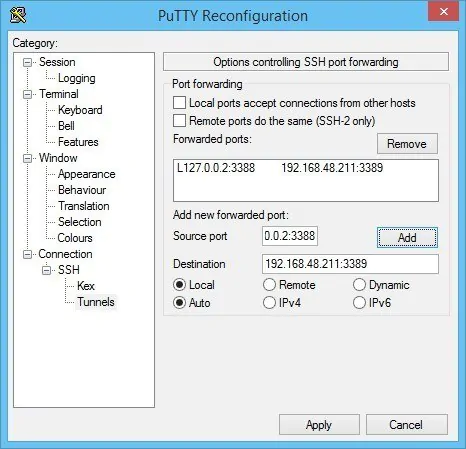
Windows 11 and WSL 2 DevOps environment
In this post I describe some of the settings and changes I made to make my Windows 11 and Ubuntu WSL2 into a fully fledged development environment. Here are the settings and tools I use for DevOps / SysOps on Windows.