Connect to a KVM host through an ssh tunnel and arbitrary port in Windows 11 and WSL 2
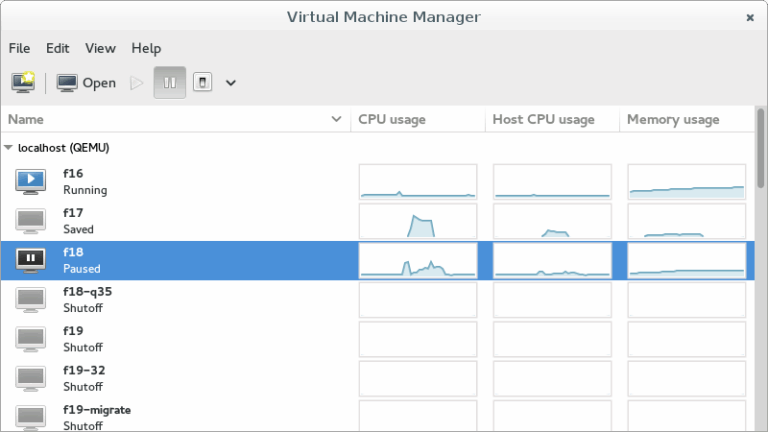
Connect virt-manager to a KVM host through an ssh tunnel and arbitrary port in Windows using Windows 11 and WSL 2.

Connect virt-manager to a KVM host through an ssh tunnel and arbitrary port in Windows using Windows 11 and WSL 2.
In this post I describe some of the settings and changes I made to make my Windows 11 and Ubuntu WSL2 into a fully fledged development environment. Here are the settings and tools I use for DevOps / SysOps on Windows.

The postsuper command controls different types of queues in the Postfix mail system, like the deferred or hold queue. This post shows you some Postfix queue operations to maintain your mail servers.
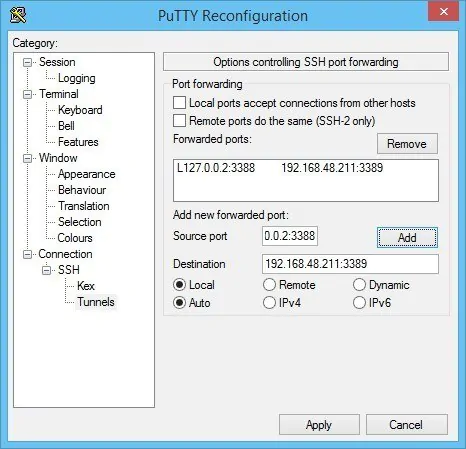
Have you ever been in a situation where you needed to perform remote administration on a Windows Server, and the RDP port 3389 is blocked on a firewall? You can tunnel RDP over SSH with PuTTY

Cconvert decimal to hex hexadecimal to decimal and Unix timestamps in Linux Bash. A quicky for my archives.

Investigate SMTP authentication issues like a boss! When using TLS encrypted SMTP connections, it's always handy if you are able to create a SMTP logon credentials and test SMTP authentication over a TLS/StartTLS connection. Preferably from your command-prompt.