Disable ECDH public server param reuse in Windows Server IIS
Windows Server IIS is known for reusing DH key values, but there is a way to disable ECDH public server param reuse in Windows Server IIS and here is how.
Windows Server IIS is known for reusing DH key values, but there is a way to disable ECDH public server param reuse in Windows Server IIS and here is how.

Learn how to create strong and unique passwords in Windows using PowerShell, because the use of those unique and strong passwords is important.

The following PowerShell snippet can be used to quickly install an SSL (or TLS) certificate in Windows Server. It assumes you have a PFX file and its password. The default location is Cert:\LocalMachine\My, to use for IIS websites.
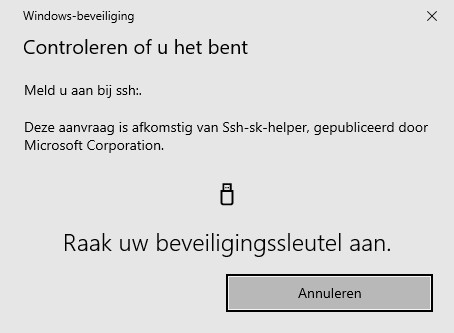
Now Win32-OpenSSH has decent support for FIDO/U2F hardware authenticators you can finally use your YubiKey for SSH authentication in Windows 11, jeej! Here is how.

If you have tens (hundreds) of servers and/or users it's easier to retrieve user SSH public keys from Active Directory (AD) than from various unmanaged authorized_keys files.
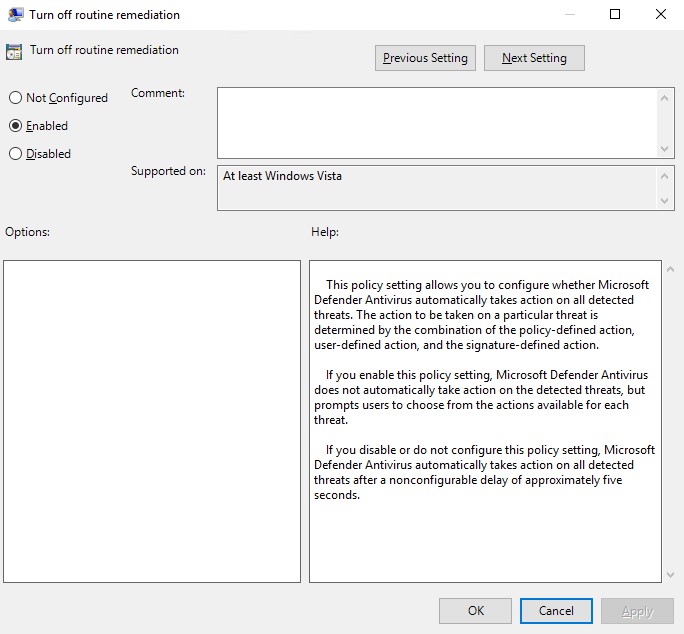
Turn off Windows Defender routine remediation using a GPO setting called “DisableRoutinelyTakingAction”. This policy setting allows you to configure whether Microsoft Defender Antivirus automatically takes action on all detected threats.
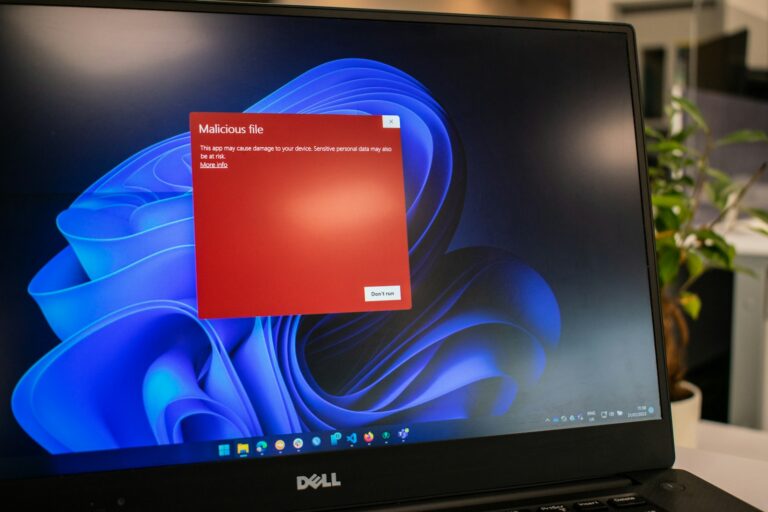
Enabling Windows Defender per GPO failed with the error message "Get-MpComputerStatus : The extrinsic Method could not be executed.", here is how to resolve this issue.
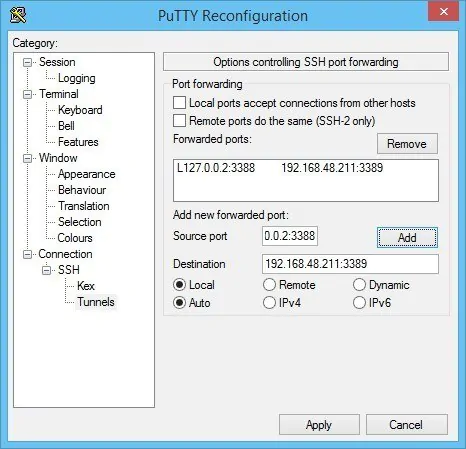
Have you ever been in a situation where you needed to perform remote administration on a Windows Server, and the RDP port 3389 is blocked on a firewall? You can tunnel RDP over SSH with PuTTY

Windows Server IIS loves to tell the world that a website runs on IIS. It does so with the "Server:" header in the HTTP response, as shown below. In this post I'll show you how to remove HTTP response headers in Windows Server IIS. You don't want to give hackers too much information about your servers, right?.

Investigate SMTP authentication issues like a boss! When using TLS encrypted SMTP connections, it's always handy if you are able to create a SMTP logon credentials and test SMTP authentication over a TLS/StartTLS connection. Preferably from your command-prompt.