Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
This post contains some example WMI filters for you to use in Group Policy Objects (GPOs) to target and manage specific Windows Server versions like 2012R2, 2016 and Windows Server 2022 / 2019.
Using Windows Management Infrastructure, or WMI, Windows admins can create filters to apply GPOs more granular on specific versions of Windows Server. In this post I provide some basic examples.
This post contains some example WMI filters for you to use in Group Policy Objects (GPOs) to target and manage specific Windows Server versions like 2012R2, 2016 and Windows Server 2022 / 2019.
If you need to target specific Windows Server versions in your Group Policy Objects (GPO’s), and you have no version differentiation in your Active Directory computer groups, then you might need WMI (or Windows Management Instrumentation) filters to target a GPO on a specific set of computers or Windows Server version. In this post I explain how to create those.
In PowerShell 5.1 you can verify WMI filters with Get-WmiObject in the Win32_OperatingSystem class:
PS C:\> Get-WmiObject -Class Win32_OperatingSystem | Select-Object Version, ProductTypePS C:\> Get-WmiObject -Class Win32_OperatingSystem | Select-Object Version,Name,ProductType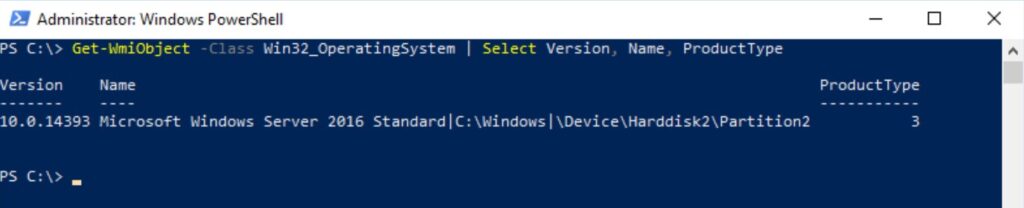
Don’t forget to use Get-CimInstance in PowerShell 7. In PowerShell 6.2 and up, the WMI v1 cmdlets, like Get-WmiObject, are deprecated. See Breaking Changes for PowerShell 6.x. You now have to use CIM (aka WIM v2), like for example Get-CimInstance:
PS C:\Users\Jan Reilink> Get-CimInstance -Class Win32_OperatingSystem | Select Version,Name,ProductType
Version Name ProductType
------- ---- -----------
10.0.22631 Microsoft Windows 11 Enterprise|C:\Windows|\Device\Harddisk0\Partition3 1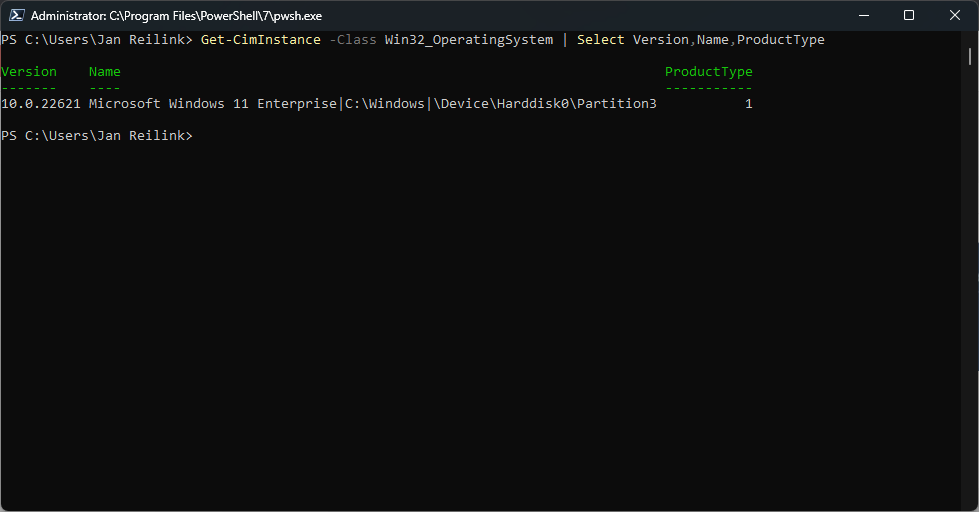
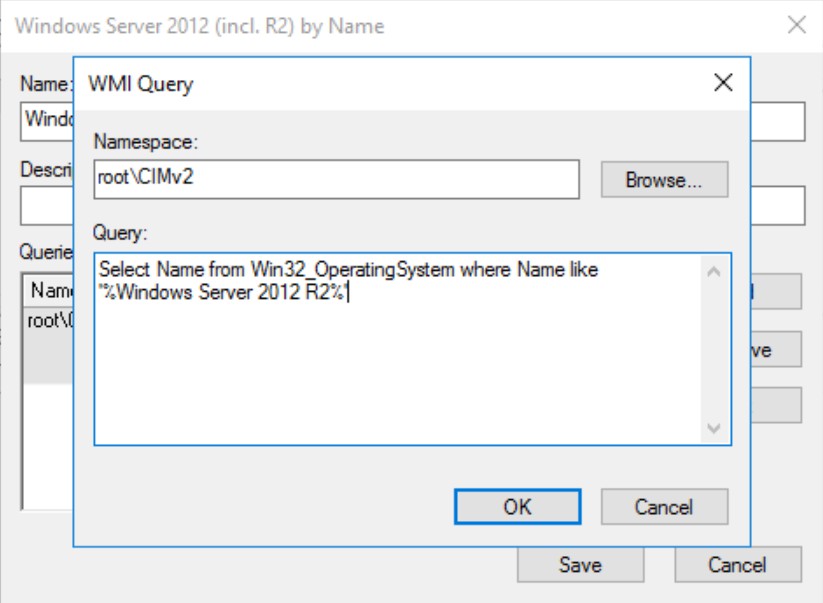
When selecting Name, it’s easy to select Windows Server 2012 R2. It’s recommended to use a LIKE sub-selection
Select Name From Win32_OperatingSystem Where Name Like '%Windows Server 2012 R2%'
Need to make WMI more robust?
In a nutshell I’ll provide some easy to us WMI filter examples:
# Windows Server 2012 en 2016 by Name
Select Name From Win32_OperatingSystem Where Name like '%Windows Server 2012 R2%' Or Name Like '%Windows Server 2016%'# Windows Server 2016 by Version
Select Version From Win32_OperatingSystem Where Version Like "10.0.14%"Why did I use “Like “10.0.14%”“? Simply because Windows Server 2019’s version number also starts with 10.0. So by not adding .14 I’d also match Windows Server 2019:
# Windows Server 2016 en 2019 by Version
Select Version From Win32_OperatingSystem Where Version Like "10.0%"And finally to only target Windows Server 2019:
# Windows Server 2019 by Version
Select Version From Win32_OperatingSystem Where Version Like "10.0.17%"Want to match Windows Server 2022 in a GPO WMI Filter, so you can enable HTTP/3 in Windows Server 2022 only, use the following WQL (WMI Query):
# Windows Server 2022 by Version
SELECT Version FROM Win32_OperatingSystem WHERE Version LIKE "10.0.20%"In PowerShell, this gives you
Get-CimInstance -Namespace root\cimv2 -Query "SELECT Version FROM Win32_OperatingSystem WHERE Version LIKE '10.0.20%'" | Select Version
Version
-------
10.0.20348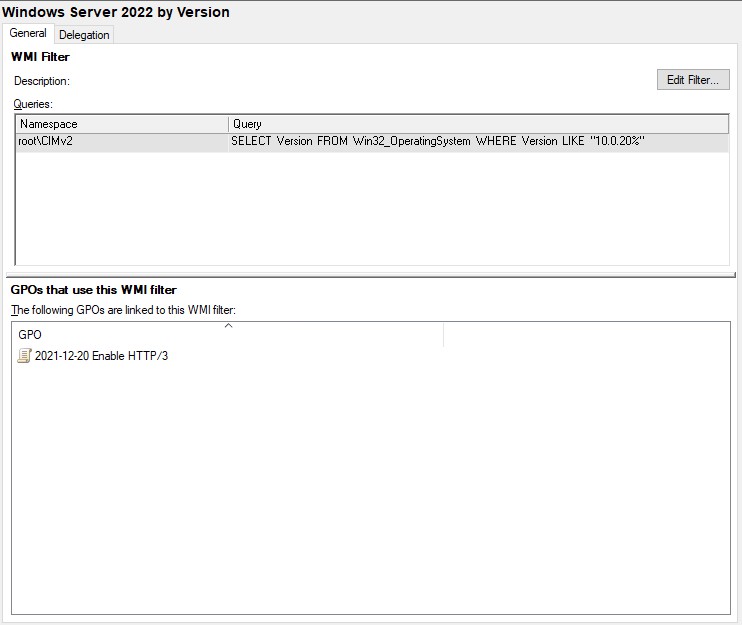
If you need to match a computer name in your GPO WMI Filter, you can use the following:
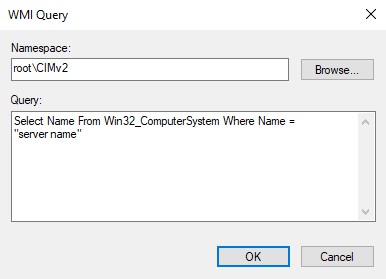
Select Name From Win32_ComputerSystem Where Name = "server name"Using this, an GPO is only applied if the computer – or server – name matches. Otherwise it is filtered out.
If you want to filter out one or two specific hosts, you can negate your query by using NOT LIKE in a WMI query. The syntax is very confusing and not intuitive. Here is how to do a WMI query for items that are NOT what you want:
Get-CimInstance -Namespace root\cimv2 -Query "SELECT Name FROM Win32_ComputerSystem WHERE NOT (Name LIKE 'host-a%') and NOT (Name like 'host-b%')" | Select-Object NameUsing WMI filters like these in Group Policy Management Console, you can fine-tune your GPO targetting. It is a powerful tool in your automation. If needed, you can even query the hardware manufacturer in your script:
(Get-CimInstance -ClassName Win32_ComputerSystem).Manufacturer“Rasta Mouse” has a lot of informative information about OUs and GPOs and WMI Filters. If you are into creating and using such WMI filters, be sure to read the blog post.




Please take a second to support Sysadmins of the North and donate!
Your generosity helps pay for the ongoing costs associated with running this website like coffee, hosting services, library mirrors, domain renewals, time for article research, and coffee, just to name a few.