Although Windows Server IIS tends to reuse DH key values, you can disable ECDH public server parameter reuse – here’s how.
Learn how to disable ECDH public server param reuse in IIS and Windows Server by setting the registry value for EphemKeyReuseTime to 0.
ECDH public server param reuse is when a server uses the same DH (Diffie-Hellman) key value for multiple handshakes, instead of generating a new one for every handshake. They should be “ephemeral” though which is why it is called “DHE” or “ECDHE”, and this means the key is single-use and should never be reused. Windows Server IIS is known for reusing DH key values, but there is a way to disable ECDH public server param reuse in Windows Server IIS.

In fact generating a new NIST P-256 ECDH or X25519 key is cheap. There is no need to reuse it for performance reasons. Unfortunately IIS does this for some reason. Disabling ECDH public server param reuse makes sure a key is not cached and then a new key is generated for every handshake. Reusing keys might get exploited.

Disable ECDH public server param reuse in the Windows registry
Set a less documented registry key EphemKeyReuseTime to 0. This forces a new key generation for every connection.
Follow these steps:
- open the Registry Editor (regedit
- navigate to
HKLM\System\CurrentControlSet\Control\SecurityProviders\Schannel\KeyExchangeAlgorithms\ECDH- if the registry key ECDH doesn’t exist you can create it.
- in ECDH click New > DWORD (32-bit) value
- Value name: EphemKeyReuseTime
- Value data: 0

Using PowerShell:
if(!(Test-Path "hklm:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\ECDH")) {
New-Item "hklm:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms" -name "ECDH"
}
New-ItemProperty "hklm:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\ECDH" -Name EphemKeyReuseTime -Value 0 -PropertyType DWordWhile you are at it, add your own checks and validation in the PowerShell code to make it more robust.
Sources:
- https://learn.microsoft.com/en-us/answers/questions/781315/ecdh-public-server-param-reuse-in-kestrel
- https://serverfault.com/a/1155857
Frequently Asked Questions
“ECDH public server param reuse” is when a server uses the same DH key value for multiple handshakes, instead of generating a new one for every handshake. The DH should be “ephemeral”, that is why it’s called “DHE” or “ECDHE”, and this means the key is single-use and should never be reused.
Generating a new NIST P-256 ECDH or X25519 key is cheap, so there is no need to reuse it for performance reasons, but some SSL accelerator appliances do that. This is bad and they should be patched/configured to not do that.
(source @ StackExchange)
ECDH (Elliptic Curve Diffie-Hellman) is a key agreement protocol that enables two parties to establish a shared secret key over an insecure channel. This shared secret can be used directly as a key or to derive another symmetric key for secure communication. It’s important to note that ECDH itself doesn’t provide authentication; it only establishes a shared secret.
You can disable this via Registry Editor. Just go to HKLM\System\CurrentControlSet\Control\SecurityProviders\Schannel\KeyExchangeAlgorithms\ECDH create a value (DWORD (32-bit)) named EphemKeyReuseTime and set it to `0`.

Did you like this post?
Please take a second to support Sysadmins of the North and donate! ❤️
Your generosity helps pay for the ongoing costs associated with running this website like coffee, hosting services, library mirrors, domain renewals, time for article research, and coffee, just to name a few. ❤️
Conclusion
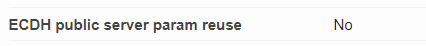
In this post you learned how to disable ECDH public server param reuse in Windows Server IIS by adding setting a registry value name EphemKeyReuseTime with value 0. Afterwards you use Qualys SSL Labs to verify whether or not public server param reuse is properly turned off.
Summary
- Learn how to disable public param reuse in IIS and Windows Server by setting the registry value EphemKeyReuseTime to 0.
- ECDH public server param reuse occurs when a server reuses the same DH key for multiple handshakes instead of generating a new one every time.
- Visual steps in the Registry Editor guide you to create the necessary ECDH value and set it to 0 for secure connections.
- You can also use PowerShell to enhance checks and validation for this process.
- After making changes, verify if public server param reuse is disabled using Qualys SSL Labs.





