Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Windows Server IIS loves to tell the world that a website runs on IIS. It does so with the "Server:" header in the HTTP response, as shown below. In this post I'll show you how to remove HTTP response headers in Windows Server IIS. You don't want to give hackers too much information about your servers, right?.
In this post I show you how to remove HTTP response headers in Windows Server and ASP.NET, after installing IIS using web.config files. This makes it a tiny bit harder for hackers and improves your server and website security. Stop giving hackers too much information.
Windows Server IIS loves to tell the world that a website runs on IIS. It does so with the “Server:” header in the HTTP response, as shown below. In this post I’ll show you how to remove HTTP response headers in Windows Server IIS. You don’t want to give hackers too much information about your servers, right?

Even though I’m not a big fan of security by obscurity (are you?), removing common server response headers is often advised by security experts. Attackers might gain a lot of information about your server and network, just by looking at the response headers a web server returns.
Therefore it’s advised you remove at least some of these headers.
But let’s start with how a normal HTTP HEAD response looks like:
HTTP/1.1 200 OK
Content-Length: 0
Content-Type: text/html; charset=UTF-8
Vary: Accept-Encoding
Server: Microsoft-IIS/8.0
X-UA-Compatible: IE=Edge,chrome=1
Date: Sun, 06 Jul 2014 10:05:34 GMT
Connection: closeHere you notice IIS displaying its version information in a Server header, as response:
Server: Microsoft-IIS/8.0As with removing ETag headers in IIS, you can rewrite and empty the Server: HTTP response header in IIS with a URL Rewrite Module outboundRule.
In older IIS versions (IIS 7, 8.5, 8.0, 8.5) you cannot really remove the Server header. But you can rewrite its content and empty it. Here you use an URL Rewrite Module outboundRule to remove the web server version information from the Server: header response.
Use the following URL Rewrite Outbound rule for example:
<rewrite>
<outboundRules rewriteBeforeCache="true">
<rule name="Remove Server header">
<match serverVariable="RESPONSE_Server" pattern=".+" />
<action type="Rewrite" value="" />
</rule>
</outboundRules>
</rewrite>What the outboundRule does is:
Server: in the output response stream, and rewrites the value with an empty string (nothing).The end result is an empty Server: response header line:
HTTP/1.1 200 OK
Content-Length: 0
Content-Type: text/html; charset=UTF-8
Vary: Accept-Encoding
Server:
X-UA-Compatible: IE=Edge,chrome=1
Date: Sun, 06 Jul 2014 10:06:08 GMT
Connection: closeYou’ve now successfully removed the Server version response from the HTTP headers!
This is a website-specific rule. If you want to create the rule for all of your applications, you have to create the rule at the server level. Also, some applications, especially third party applications, may require and depend on the Server header. Then you may need to remove this rule for those applications.
How to enable HTTP Strict-Transport-Security (HSTS) on IIS
The fun part of rewriting response headers is that you can display your own information string. For example, if you give in an value in the Rewrite action, that message is displayed:
<action type="Rewrite" value="Saotn Server Software systems, LTD." />HTTP/1.1 200 OK
Content-Length: 0
Content-Type: text/html; charset=UTF-8
Vary: Accept-Encoding
Server: Saotn Server Software systems, LTD.
X-UA-Compatible: IE=Edge,chrome=1
Date: Sun, 06 Jul 2014 11:19:16 GMT
Connection: closeThis is fun, or isn’t it? 🙂
In IIS 10.0 (Windows Server 2022 / 2019 / 2016), you can remove the Server header by configuring requestFiltering in your web.config system.webServer node:
<security>
<requestFiltering removeServerHeader ="true" />
</security>In IIS Manager Configuration Editor:
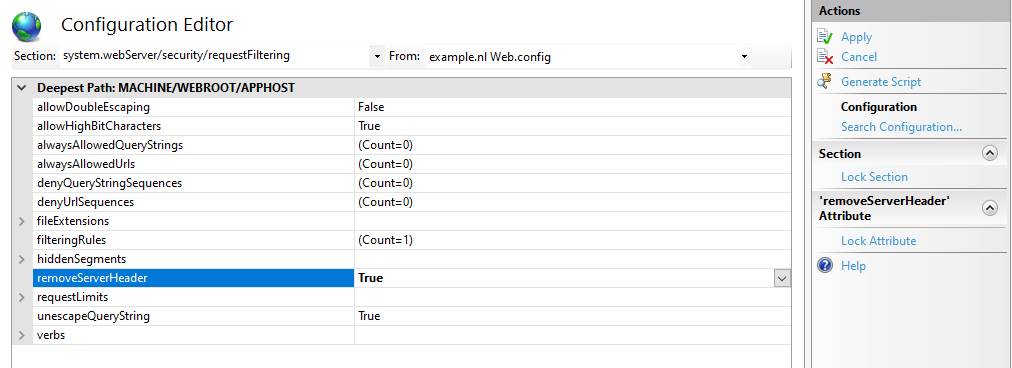
Set removeServerHeader to True in IIS Configuration Manager requestFiltering node. You find this in the Internet Information Services Manager tool.
Or using AppCmd.exe / PowerShell:
C:\Windows\System32\inetsrv\appcmd.exe `
set config `
-section:system.webServer/security/requestFiltering `
/removeServerHeader:'True' `
/commit:apphostSet-WebConfigurationProperty `
-pspath 'MACHINE/WEBROOT/APPHOST/' `
-filter 'system.webServer/security/requestFiltering' `
-name 'removeServerHeader' `
-value 'True'This way you don’t have to fiddle with complex outbound rewrite rules. To remove ASP.NET’s X-Powered-By header you still need the customHeaders section as mentioned below.
After setting removeServerHeader to True, it’s recommended to verify this setting. In PowerShell you can use IISAdministration module, the output must be “True”:
Get-IISConfigSection -SectionPath "system.webServer/security/requestFiltering" | Get-IISConfigAttributeValue -AttributeName "removeServerHeader"
TrueWith AppCmd.exe you have to look through the XML output:
c:\windows\system32\inetsrv\appcmd.exe list config -section:system.webServer/security/requestFiltering
<system.webServer>
<security>
<requestFiltering removeServerHeader="true">
<!-- ... -->By default IIS tells the world it’s powered by ASP.NET, by placing an X-Powered-By header:
HTTP/1.1 200 OK
Content-Length: 0
Content-Type: text/html; charset=UTF-8
Vary: Accept-Encoding
Server:
X-Powered-By: ASP.NET
X-UA-Compatible: IE=Edge,chrome=1
Date: Sun, 06 Jul 2014 10:07:37 GMT
Connection: closeThis response header can be removed with a customHeaders setting in web.config, placed in the <system.webServer> node:
<httpProtocol>
<customHeaders>
<remove name="X-Powered-By" />
</customHeaders>
</httpProtocol>Remove X-Powered-By header with PowerShell:
Clear-WebConfiguration `
-pspath "IIS:\\" -filter "/system.webServer/httpProtocol/customHeaders/add[@name='X-Powered-By']"Now the X-Powered-By header is removed from the response header output
HTTP/1.1 200 OK
Content-Length: 0
Content-Type: text/html; charset=UTF-8
Vary: Accept-Encoding
Server:
X-UA-Compatible: IE=Edge,chrome=1
Date: Sun, 06 Jul 2014 10:10:02 GMT
Connection: closeThe X-AspNet-Version HTTP Header broadcasts to the world what version of ASP.NET is used. Add the following content inside the <system.web> node in your application’s web.config file:
<httpRuntime enableVersionHeader="false" />



Please take a second to support Sysadmins of the North and donate!
Your generosity helps pay for the ongoing costs associated with running this website like coffee, hosting services, library mirrors, domain renewals, time for article research, and coffee, just to name a few.
This post showed you various methods of removing the Server response header in IIS, using either a URL Rewrite Module outboundRule or requestFiltering property removeServerHeader. It also showed you how to remove ASP.NET’s X-Powered-By and X-Aspnet-Version headers.