Do you need to tunnel Remote Desktop over SSH with PuTTY? Have you ever been in a situation where you needed to perform remote administration on a Windows Server, and the RDP port 3389 is blocked on a firewall? You can tunnel RDP over SSH with PuTTY. This particularly comes in handy when there is no VPN available to the remote network…
To tunnel Remote Desktop Protocol over ssh using PuTTY, all you need is an account on the premises. For example a firewall or Linux server with ssh access, and PuTTY on your Windows desktop.
Proxy connections with SSH
SSH can proxy connections both forward and backwards. It creates a secure connection between a local computer and a remote machine through which services can be relayed. Because the connection is encrypted, SSH tunneling is useful for transmitting information that uses an unencrypted protocol, such as IMAP, VNC, or IRC. And RDP 🙂
SSH can proxy connections both forward and backwards, by opening a port on either the local machine running the SSH client, or the remote SSH server. If you have privileges to do so of course.
For example, if you want to connect to a remote host on RDP port 3389, but you don’t have direct access to reach that machine because of firewall or network restrictions, the SSH client can listen on a local port and pretend that it is the remote machine. All connections to that port will be sent through the SSH server to the remote host.
Learn how to share OpenSSH keys with WSL in Windows 10
Reconfigure PuTTY for Remote Desktop Protocol (RDP) tunneling through ssh
To tunnel Remote Desktop Protocol over ssh using PuTTY, all you need is an account on the premises. For example a firewall or Linux server with ssh access, and PuTTY on your Windows desktop. PuTTY is a nifty ssh client for Windows that you can download here.
For Windows, PuTTY is the de-facto standard SSH client.
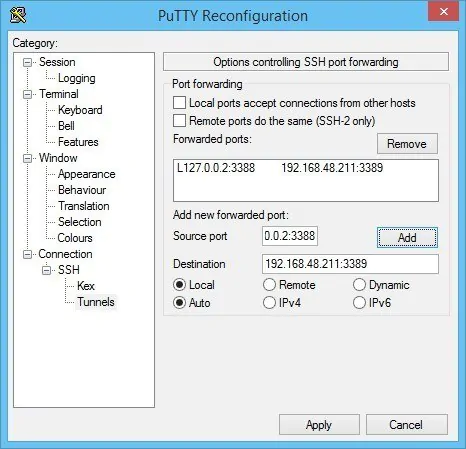
Once you are connected to your remote network with ssh/PuTTY, you need to reconfigure the connection to support SSH-tunneling. In the PuTTY Reconfiguration screen, go to Connection → SSH → Tunnels. This is where we can set up an SSH tunnel for Remote Desktop.
Under Source port, add your local IP address and port. Because the RDP 6+ client in Windows has issues with the loopback to TCP Port 3390, you need to use a different port. I use TCP port 3388 on IP address 127.0.0.2, and my remote internal IP address and RDP port 3389 as Destination (192.168.48.211:3389). See the image:
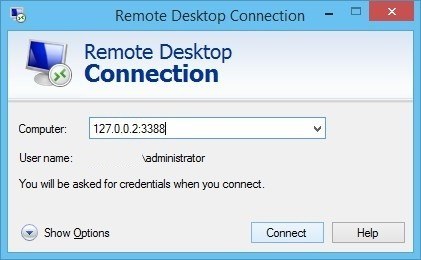
After clicking Apply, the SSH-tunnel for remote desktop is active, and you can connect the Remote Desktop Connection to 127.0.0.2:3388:
Tunnel RDP using OpenSSH and PowerShell in Windows 11
If you have the OpenSSH client installed in Windows 11 (/10), then you can use a command similar to Linux’ ssh tunnel:
ssh -N -L 13389:[Windows Server RDP address]:3389 [address ssh server] -l [ssh username]To ease the usage, I wrapped in a PowerShell script, that connects to my on-premises stepping-stone host with ssh:
$remHost = (Read-host -Prompt ("RDP host: "))
Write-Output "Setting up an SSH RDP tunnel with ${remHost}"
Start-Process ssh -ArgumentList "-N -L 13389:${remHost}:3389 -l [ssh username] steppingstone-host.example" -Verb open
[void](Read-Host 'Press Enter to continue...')
&mstsc /V:localhost:13389 /w:800 /h:600 /promptUse this PowerShell one-liner to verify whether OpenSSH client is installed on your Windows 10 system. It should print Installed.
(Get-WindowsCapability -Online | ? Name -like 'OpenSSH.Client*').StateYou find more ssh tips in my post Windows 11/10 and WSL 2 DevOps environment.
How to tunnel Windows Remote Desktop (RDP) through ssh on Linux
When you are in a situation where you are on a Linux work station and need to tunnel RDP through ssh in Linux, you can use the following ssh port forwarding, or tunnel (assuming you have an on-premise Linux server to SSH into to set up the port forward):
ssh port forwarding / tunnel set-up for RDP
ssh -N -L 13389:[Windows Server RDP address]:3389 [address ssh server] -l [ssh username]Now you can connect your RDP client to 127.0.0.1:13389 as if it were the remote server.
Some Remote Desktop clients for Linux are:
- KRDC – KRDC is a client application that allows you to view or even control the desktop session on another machine that is running a compatible server. VNC and RDP is supported
- Remmina – A feature rich Remote Desktop Application for Linux and other Unixes
- rdesktop – rdesktop is an open source UNIX client for connecting to Windows Remote Desktop Services, capably of natively speaking Remote Desktop Protocol (RDP) in order to present the user’s Windows desktop
- xfreerdp – FreeRDP is a free implementation of the Remote Desktop Protocol (RDP), released under the Apache license
Or do you need to change port forwarding options in an existing ssh connection?
Tunnel ssh using sshuttle
Another great option is to tunnel ssh using sshuttle, on GNU/Linux. From its manpage:
sshuttle allows you to create a VPN connection from your machine to any remote server that you can connect to via ssh, as long as that server has python 2.3 or higher.
To work, you must have root access on the local machine, but you can have a normal account on the server.It’s valid to run sshuttle more than once simultaneously on a single client machine, connecting to a different server every time, so you can be on more than one VPN at once.
If run on a router, sshuttle can forward traffic for your entire subnet to the VPN.
If you have a hop (steppingstone) on-premises, you can use the following sshuttle example:
sshuttle -r username@steppingstone-host.example 192.168.0.0/16This’ll easily create a VPN (Virtual Private Network) connection from your machine to any remote server that you can connect to via ssh.




Did you like this post?
Please take a second to support Sysadmins of the North and donate!
Your generosity helps pay for the ongoing costs associated with running this website like coffee, hosting services, library mirrors, domain renewals, time for article research, and coffee, just to name a few.



[…] Tunnel RDP through SSH & PuTTY, or learn how to share OpenSSH keys with WSL in Windows 10 […]
[…] you know you can tunnel RDP connections through SSH? This comes in very handy if your Windows Servers are behind a firewall or […]