Windows Server IIS loves to tell the world that a website runs on IIS. It does so with the Server: header in the HTTP response, as shown below. In this post I'll show you how to remove HTTP response headers in Windows Server IIS. You don't want to give hackers too much information about your servers, right?.
In this post I show you how to remove HTTP response headers in Windows Server and ASP.NET, after installing IIS using web.config files. This makes it a tiny bit harder for hackers and improves your server and website security. Stop giving hackers too much information.
Normal HTTP Response headers
Even though I'm not a big fan of security by obscurity (are you?), removing common server response headers is often advised by security experts. Attackers might gain a lot of information about your server and network, just by looking at the response headers a web server returns.
Therefore it's advised you remove at least some of these headers.
But let's start with how a normal HTTP HEAD response looks like:
HTTP/1.1 200 OKContent-Length: 0Content-Type: text/html; charset=UTF-8Vary: Accept-EncodingServer: Microsoft-IIS/8.0X-UA-Compatible: IE=Edge,chrome=1Date: Sun, 06 Jul 2014 10:05:34 GMTConnection: closeHere you notice IIS displaying its version information in a Server header, as response:
Server: Microsoft-IIS/8.0As with removing ETag headers in IIS, you can rewrite and empty the Server: HTTP response header in IIS with a URL Rewrite Module outboundRule.
Remove Server response header with an outboundRule URL Rewrite rule
In older IIS versions (IIS 7, 8.5, 8.0, 8.5) you cannot really remove the Server header. But you can rewrite its content and empty it. Here you use an URL Rewrite Module outboundRule to remove the web server version information from the Server: header response.
Use the following URL Rewrite Outbound rule for example:
<rewrite> <outboundRules rewriteBeforeCache="true"> <rule name="Remove Server header"> <match serverVariable="RESPONSE_Server" pattern=".+" /> <action type="Rewrite" value="" /> </rule> </outboundRules></rewrite>What the outboundRule does is:
- it looks for the header - or serverVariable -
Server:in the output response stream, and rewrites the value with an empty string (nothing).
The end result is an empty Server: response header line:
HTTP/1.1 200 OKContent-Length: 0Content-Type: text/html; charset=UTF-8Vary: Accept-EncodingServer:X-UA-Compatible: IE=Edge,chrome=1Date: Sun, 06 Jul 2014 10:06:08 GMTConnection: closeYou've now successfully removed the Server version response from the HTTP headers!
This is a website-specific rule. If you want to create the rule for all of your applications, you have to create the rule at the server level. Also, some applications, especially third party applications, may require and depend on the Server header. Then you may need to remove this rule for those applications.
Rewrite 'Server: Microsoft-IIS/8.0' with your own server information - just for the fun
The fun part of rewriting response headers is that you can display your own information string. For example, if you give in an value in the Rewrite action, that message is displayed:
<action type="Rewrite" value="Saotn Server Software systems, LTD." />HTTP/1.1 200 OKContent-Length: 0Content-Type: text/html; charset=UTF-8Vary: Accept-EncodingServer: Saotn Server Software systems, LTD.X-UA-Compatible: IE=Edge,chrome=1Date: Sun, 06 Jul 2014 11:19:16 GMTConnection: closeIsn't this fun, now is it? :)
removeServerHeader requestFiltering in IIS 10.0
In IIS 10.0 (Windows Server 2022/2019/2016), you can remove the Server header by configuring requestFiltering in your web.config system.webServer node:
<security> <requestFiltering removeServerHeader ="true" /></security>In IIS Manager Configuration Editor:
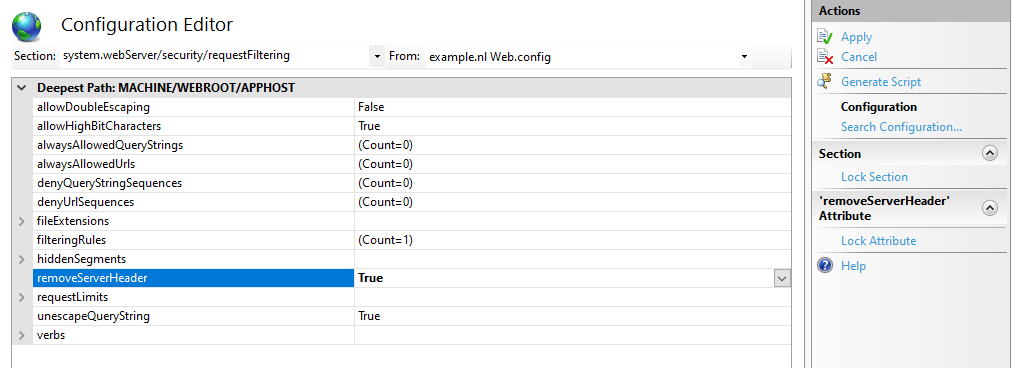
Or using AppCmd.exe / PowerShell:
C:\Windows\System32\inetsrv\appcmd.exe set config -section:system.webServer/security/requestFiltering /removeServerHeader:'True' /commit:apphostSet-WebConfigurationProperty -pspath 'MACHINE/WEBROOT/APPHOST/' -filter 'system.webServer/security/requestFiltering' -name 'removeServerHeader' -value 'True'This way you don't have to fiddle with complex outbound rewrite rules. To remove ASP.NET's X-Powered-By header you still need the customHeaders section as mentioned below.
Verify setting removeServerHeader with PowerShell and AppCmd.exe
After setting removeServerHeader to True, it's recommended to verify this setting. In PowerShell you can use IISAdministration module, the output must be "True":
Get-IISConfigSection -SectionPath "system.webServer/security/requestFiltering" | Get-IISConfigAttributeValue -AttributeName "removeServerHeader"TrueWith AppCmd.exe you have to look through the XML output:
c:\windows\system32\inetsrv\appcmd.exe list config -section:system.webServer/security/requestFiltering<system.webServer> <security> <requestFiltering removeServerHeader="true"><!-- ... -->Remove ASP.NET 'X-Powered-By' header in IIS using web.config customHeaders
By default IIS tells the world it's powered by ASP.NET, by placing an X-Powered-By header:
HTTP/1.1 200 OKContent-Length: 0Content-Type: text/html; charset=UTF-8Vary: Accept-EncodingServer:X-Powered-By: ASP.NETX-UA-Compatible: IE=Edge,chrome=1Date: Sun, 06 Jul 2014 10:07:37 GMTConnection: closeThis response header can be removed with a customHeaders setting in web.config, placed in the <system.webServer> node:
<httpProtocol> <customHeaders> <remove name="X-Powered-By" /> </customHeaders></httpProtocol>Remove X-Powered-By header with PowerShell:
Clear-WebConfiguration -pspath "IIS:\\" -filter "/system.webServer/httpProtocol/customHeaders/add[@name='X-Powered-By']"Now the X-Powered-By header is removed from the response header output
HTTP/1.1 200 OKContent-Length: 0Content-Type: text/html; charset=UTF-8Vary: Accept-EncodingServer:X-UA-Compatible: IE=Edge,chrome=1Date: Sun, 06 Jul 2014 10:10:02 GMTConnection: closeX-AspNet-Version header
The X-AspNet-Version HTTP Header broadcasts to the world what version of ASP.NET is being used. Add the following content inside the <system.web> node in your application's web.config file:
<httpRuntime enableVersionHeader="false" />
Thank you very much! <3 ❤️

Hi, my name is Jan. I am not a hacker, coder, developer or guru. I am merely an application manager / systems administrator, doing my daily thing at Embrace – The Human Cloud. In the past I worked at CLDIN (CLouDINfra) and Vevida. With over 20 years of experience, my specialties include Windows Server, IIS, Linux (CentOS, Debian), security, PHP, websites & optimization. I blog at https://www.saotn.org.

Pingback: Install IIS in Windows 11 using PowerShell
It will not work after reloading a page. It will give IIS version after reloading or refreshing a page.
Please go for link it will work like charm.
https://stackoverflow.com/questions/22401219/remove-server-response-header-iis-8-0-8-5
Hi Ketan,
What exactly did you do (configure in your
web.config)? What did you expected it to do? And what was the result? If it’s not working working for you, and IIS still prints its name, then you did something wrong in yourweb.configfile (there are different methods for different builds of Windows Server IIS), or you have some type of middleware intervening.Hi
if i will send wrong request the server version is showing like below .
HTTP/1.1 400 Bad Request
Content-Type: text/html; charset=us-ascii
Server: Microsoft-HTTPAPI/2.0
Date: Mon, 27 Apr 2020 09:57:10 GMT
Connection: close
How to remove Server: Microsoft-HTTPAPI/2.0
Content-Length: 334
Hi,
We’re using URL Rewrite Outbound rule to clear the value of the Server header and it works when using GET or POST, but when we use HEAD method is would still show IIS 8.5.
Any ideas why? The only difference I see is that we’re not using “rewriteBeforeCache=true”. Could that be the issue?
Hi Nikko,
Thank you for your comment.
At this moment I’m not sure whether the outbound rewrite rule triggers on a HEAD request. Unfortunately, I’m lacking the time to look it up.
The HTTP/1.1 RFC states for HEAD requests:
So it *should* produce the same output. But you could give https://forums.iis.net/ or https://stackoverflow.com/ a try for confirmation. I’m interested in the outcome.
I want to remove the text/html on response after sending the request to client as text/xml
Hi, How to remove the Response Server for the error 500?
Hello Jan,
I am looking to implement this changes for my application which is running on windows server..
Could you please help to share exact file name where I need to add above rewrite rule on window server
reason why am asking as I have implemented same fix for removing server information for port 47001 and 5985 but this is something not working for 8080 port number. It was added in web.conf file and below is response message for 8080 port
amazing man thanks a lot!!
Good day all, I am running into a problem: I succesfully created an Outbound Rule in IIS that rewrites the server header to “This is a Web Server” instead of Microsoft-IIS/7.5. However, after this the Active Directory Single Sign On is no longer working for the users. Is there another option that does not interfere with Single Sign On? It seems the server header is being used by Active Directory to authenticate. All ideas welcome!
Hi Marq! I’m sorry, but I wouldn’t know, I’m not familiar with Active Directory Single Sign On.
Perhaps the renamed Server header doesn’t match the SPN anymore? You can verify SPN’s in your domain with setspn. And you can use tools like Chrome developer tools, fiddler, etc to view and inspect all header being sent and returned. (Edit: maybe you’ve renamed too many headers by accident?)
How do you remove-unwanted-http-response-headers if you’re using adfs 3.0 since it’s not using iis?
For as far as I know, you can only use a proxy in front of ADFS to remove headers.
Thanks Jan. Great article i removed iis server headers successfully.
Great to hear David, thank you for your feedback :)
To remove all instances of the header (incl. on 404, etc. responses) or for self hosted services:
https://blogs.msdn.microsoft.com/dsnotes/2017/12/18/wswcf-remove-server-header/
Hi,
I am getting the Server Name as “Microsoft-IIS/8.5” even after rewriting the server name as “” in the Error pages. Following is the web.config code:
Hi Ankit,
Unfortunately your web.config code got lost in the comment. But what do you mean with “in the Error pages”, like the default IIS error pages located in
C:\inetpub\custerr\en-US? Or somewhere else? Perhaps you have to useexistingResponse=passthroughtoo? See the other comments.Hi Jan,
I am redirecting the error to the custom error pages like
and I am using the following to remove/rename the Server Name:
But, then also Server Name is coming in the custom error pages. How to remove the server name from the custom error pages?
Hi Ankit,
Your code isn’t coming through, please use a gist if possible and link to there, or wrap your code nicely in `<code></code>` tags.
Hi Jan,
Thanks for the advice. I hope this time my code is visible.
I am developing a mobile friendly application using MEAN. So. my issue is that I want to remove/hide/rename the Server Name from all the pages. I am able to do so in all the pages except the custom error pages. I am redirecting the error to the custom error pages like:
and I am using the following to remove/rename the Server Name:
But, then also Server Name is coming in the custom error pages. How to remove the server name from the custom error pages?
Hi Jan,
Actually, the issue is that the server name is visible in the HTTP Headers. Using the outbound rule in web.config, the server name is removed from the web pages but it is not removed from the custom error pages to which I am redirecting. I have also used errorMode=”Custom” existingResponse=”PassThrough” but it’s still coming.
When I used below code
protected void Application_BeginRequest(object sender, EventArgs e)
{
var application = sender as HttpApplication;
if (application != null && application.Context != null)
{
application.Context.Response.Headers.Remove(“Server”);
}
}
Then I am getting following error.
Error: This operation requires IIS integrated pipeline mode
More Info: I am using IIS 10, website hosting as Application and Application pool as Classic mode. If I changed to Integrated mode then working fine. But right now I can not change to this on Production environment because it may create other issue.
So, can you please suggest best solution in this situation.
Hi Rikin, thank you for your comment!
I’m not a fan of Classic mode application pools. Why would you want to have IIS 6.0 behaviour? I’d say, fix the problems you have switching to Integrated mode, and move on from there turning off response headers. If Integrated mode is really not an option, try to use web.config settings to disable headers.
HTH!
Thanks for the help!
I also have a rule that redirects http requests to https. But the redirect sends back all headers, including the Server: header. This is the http rule:
This is from the Microsoft URL Rewrite reference page:
Usage of a Redirect action implies that no subsequent rules evaluated for the current URL after redirection is performed.
Is there any way to remove the server header on a redirect?
I am using IIS 8.5 and whenever I attempt to use in my web.config IIS does not like it. I’ve seen that this only works on IIS7 or other versions. Is there a workaround or other method to remove the ASP version?
looks like it removed my code ” ” in my comment above
one more try httpRuntime enableVersionHeader “false”
Removing the server variable from response using url rewrite outbound rules is not working . application is angular 4 application and My server is windows 8 with iis 8.5 and I have my web.config data as shown below .
what is the impact,if application caching having both
Custom HTTP Response Header +set common HTTP response header
Hi, great article, but I’ve got question/problem..
At the first glance all seems be well, I receive modified http headers, but when I send request to doesn’t exists page (and server will return 404 webpage) server name is ‘IIS 8.5’ in the HTTP headers..
I found what is a problem – custom error pages.
When I remove httpErrors elements from web.config, Server Name header isn’t display in HTTP headers (in both cases – correct/incorrect webpage url).
How can I fix it ? (I want to have custom error pages and remove Server Name header..)
Regards
AErot
Hi @disqus_E1570bwNoJ:disqus , thank you for your comment. Interesting… What are you using, PHP or ASP.NET, and which solution do you use to remove the Server: header? It might be a .NET Framework thingy.
Hi Jan R, thanks for quick response. I use your method: URL Rewrite Module Outbound Rule on IIS8. Actually I created topic on forums.iis.net ( http://forums.iis.net/t/1233506.aspx?How+to+remove+Server+Name+Microsoft+IIS+8+5+from+HTTP+headers+ ) (where is my config file), but I have not received accurate answer yet.
I’m still looking for help..
Regards
AErot
I’ve seen your web.config in that thread. Maybe you have to add
existingResponse=to your custom httpErrors node? See http://stackoverflow.com/a/31041696/1297898 for more information.Bullseye! It looks like it’s working with Passthrough :) I must think about error page in ASP.NET. Thx!
Best
AErot
Nice find @disqus_E1570bwNoJ:disqus , if you have the relevant
web.configlines for me (and the scripting language you use: ASP.NET, PHP or ASP), I can add it to this post. Thanks in advance!Hi,
When i set the existingResponse=passthrough, the server information is not displayed for the 404 status code but my custom error pages defined in IIS stopped working. Is there any workaround for this?
We have tried it. But it doen’t work. Probably because of this line (MVC…): routes.IgnoreRoute(“{resource}.axd/{*pathInfo}”);
Thanks for the answer, do you have any idea how to fix this?
Have you tried the
global.asax(.cs)option?I’ve a issue with the solution.
I can do a request to /blalbla.axd (every name possible) and then the “Server” variable will have a value…
Hi Ansonmus, thanks for your comment.
The
.axdfile type is handled by the .NET Framework and often falls beyond the scope of URL Rewrite.This article was very helpful. The $2 donation is worth it.
Thank you very much, much appreciated! :)
Is there any way to completely remove “Server: Microsoft-IIS/8.0” from a site having static pages only like ?
Hi Kunal, thank you for your comment.
An IIS Outbound Rule rewrites the output stream (HTTP response), so it’ll also remove the Server header from static HTML files.